MonitorMe - Android Monitoring App
MonitorMe uses DroidTracer, which is an application-agnostic library to intercept system events on the Android platform.
How to install
1) Install the MonitorMe.apk on your phone, tablet or emulator
2) Load the DroidTracer kernel module
- First, you need to boot your device with a kernel that has kprobes enabled
- Download the kernel module for your device below and push it to your device:
adb push droidtracer.ko /storage/sdcard0/<droidtracer-kernel-module>.ko - Load the kernel module:
adb shell su -c "insmod /storage/sdcard0/<droidtracer-kernel-module>.ko"
| Device | Version | Build | DroidTracer kernel module |
|---|---|---|---|
| Nexus S | 2.3.6 | GRK39F | |
| Nexus 4 | 4.4.2 | KOT49H | [Download] |
| Nexus 5 | 5.0.1 | LRX22C | |
| Nexus 5 | 5.1.1 | LMY48B | [Download] |
| Nexus 7 | 4.3 | JWR66Y | [Download] |
| Emulator | Goldfish | [Download] |
How to use
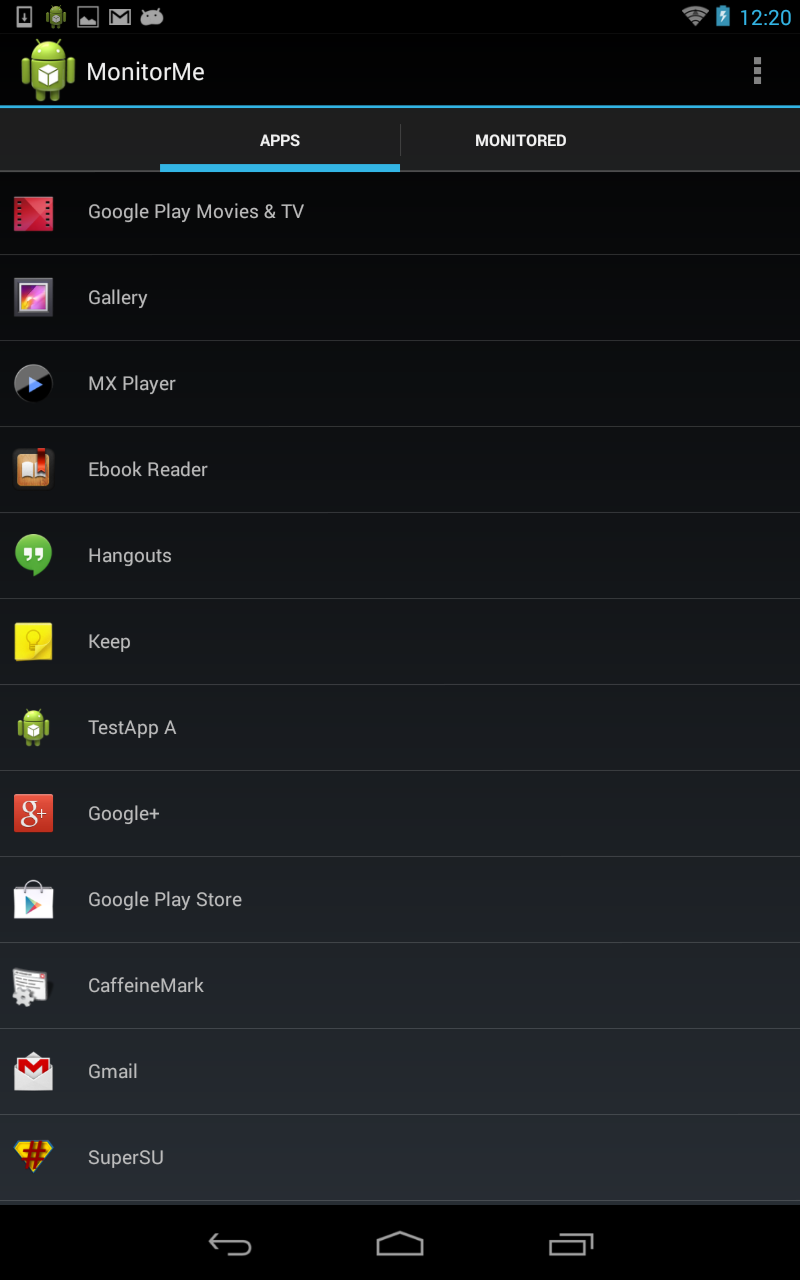
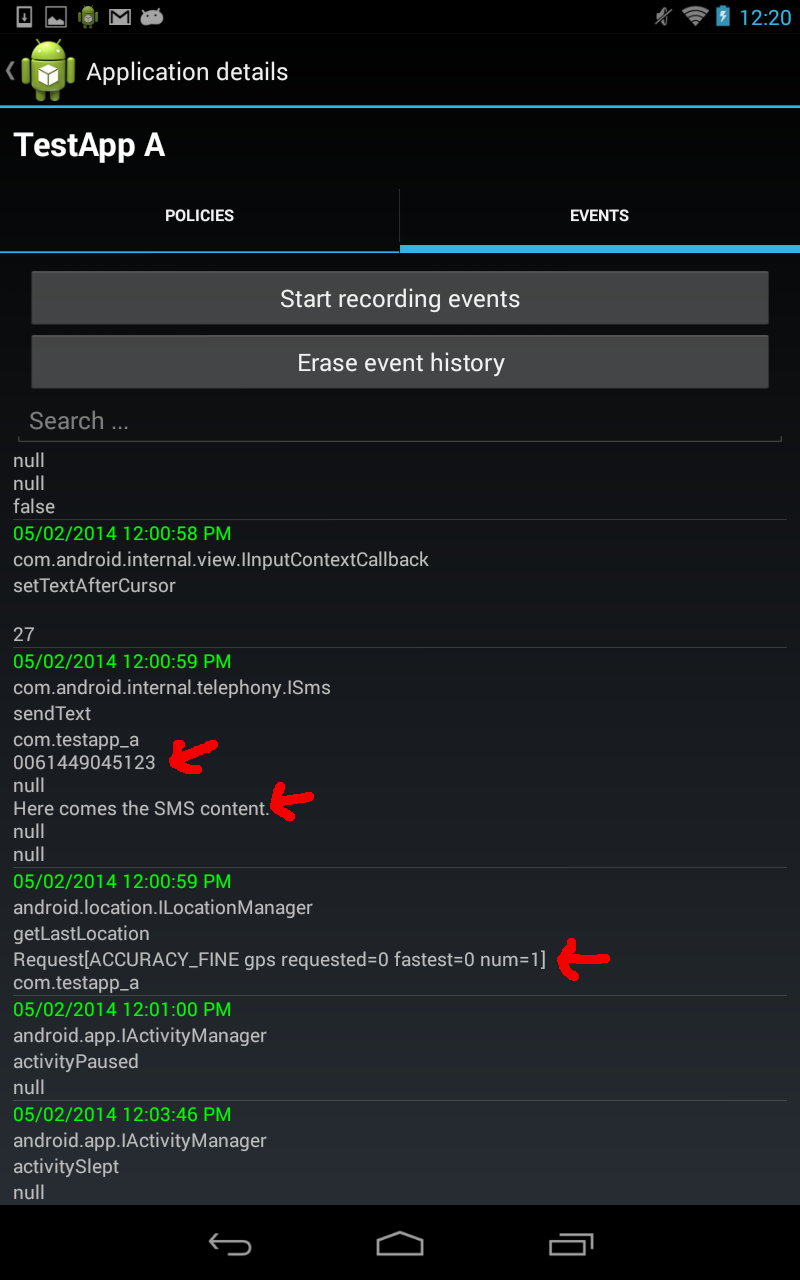
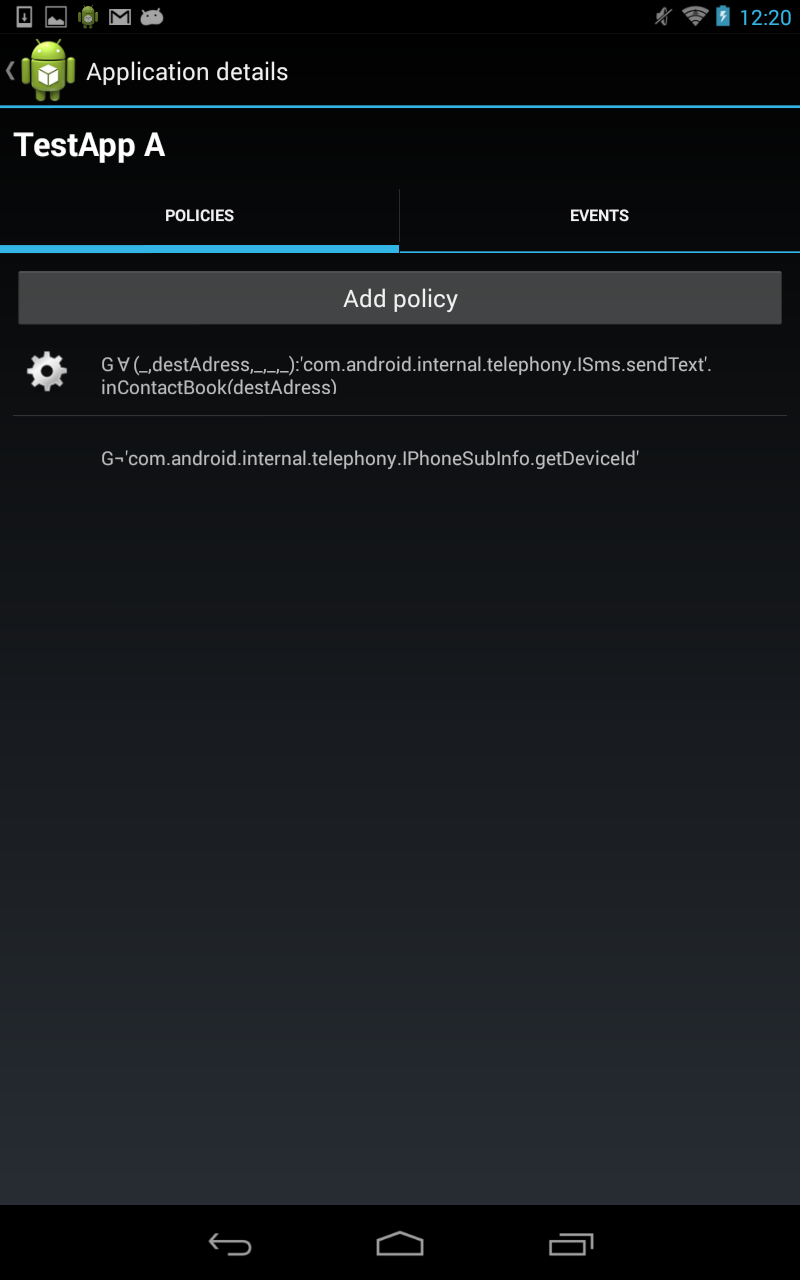
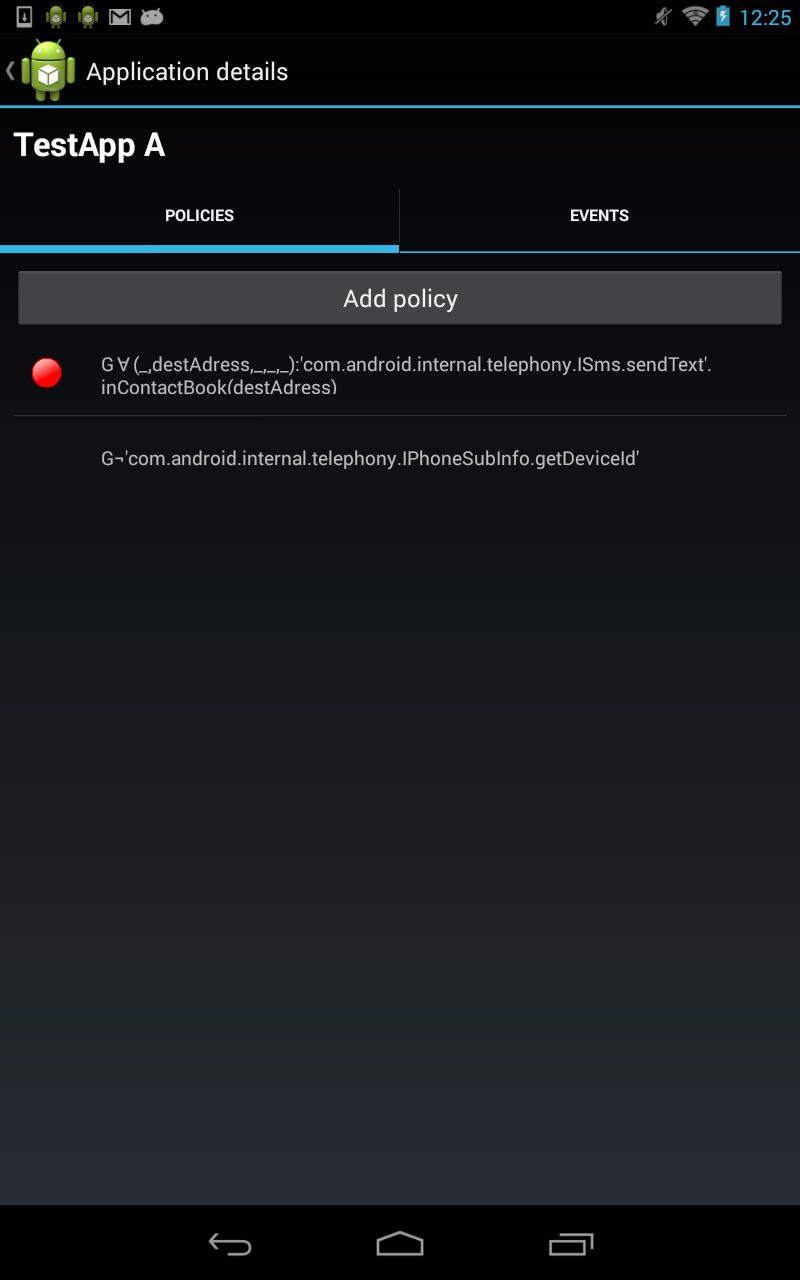
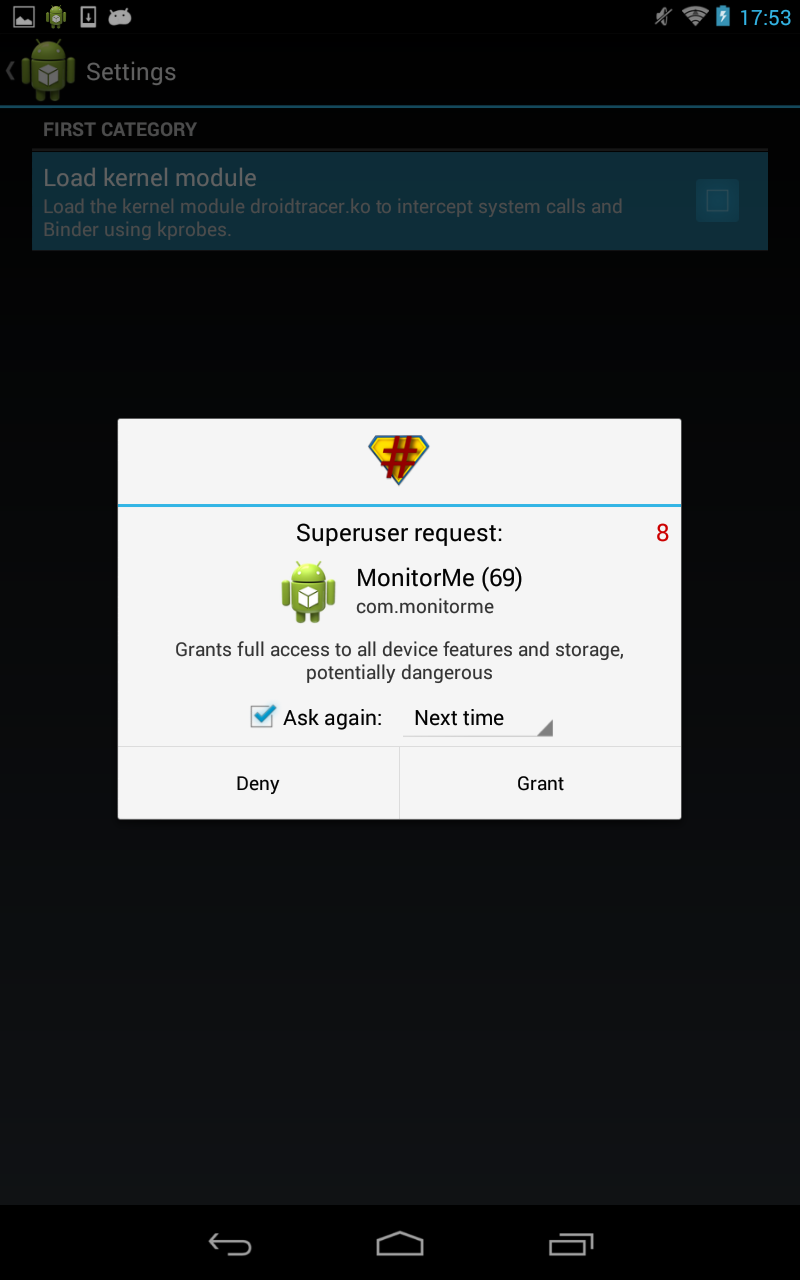
The main view of MonitorMe is shown in Figure 1. Clicking on an app in the list leads to a detail view, where you can either start recording system events for an app (Figure 2) or monitor policies for it (Figure 3). Recording system events means that occurring events are stored in a sqlite database on your device, and can be shown in form of a list on your phone. In Figure 3, you see for each event the interface and method name called (first two rows), followed by its method arguments printed as strings. See the red arrows, which show as an example the recipient and content of an SMS, as well as the location accuracy requested when getLastLocation() was called. Furthermore, another view (Figure 3) lets you select from a list of policies (and also add new policies), which you like to monitor for an app. Figure 4, shows the policy “no installed app should ever send an SMS to a phone number, which is not stored in the user’s contacts list”, which got violated by “TestApp A”.
Note that monitoring policies does not depend on recording events (both are different features of MonitorMe). The monitors associated with policies process events on the fly and do not store them explicitly, but keep an inner state if necessary to decide about the violation.
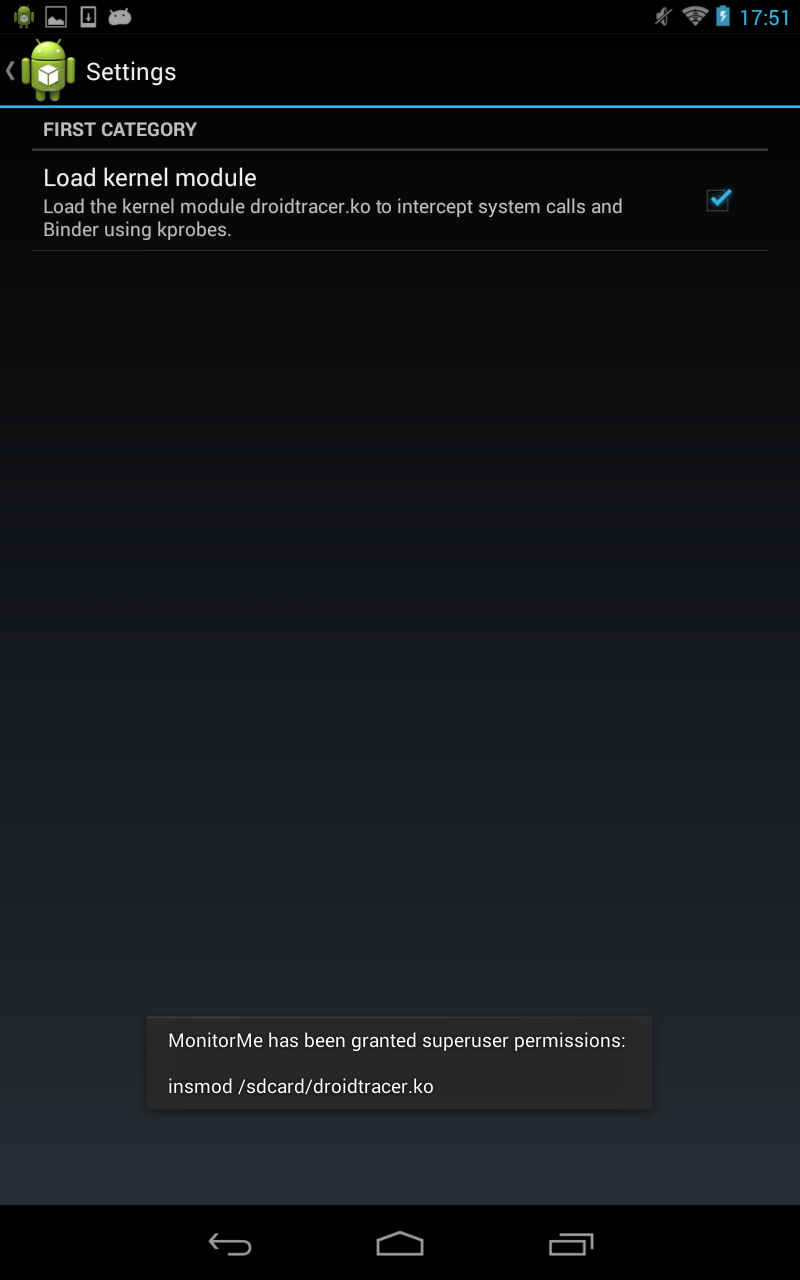
Figure 5 and 6 show, how the kernel module can be manually loaded or unloaded (if it was copied in the sdcard directory of your device before) in the settings view of MonitorMe. During this process the user is asked to grant root permission.